The Economist had a good (probably unintentional) illustration of this.

The Economist had a good (probably unintentional) illustration of this.
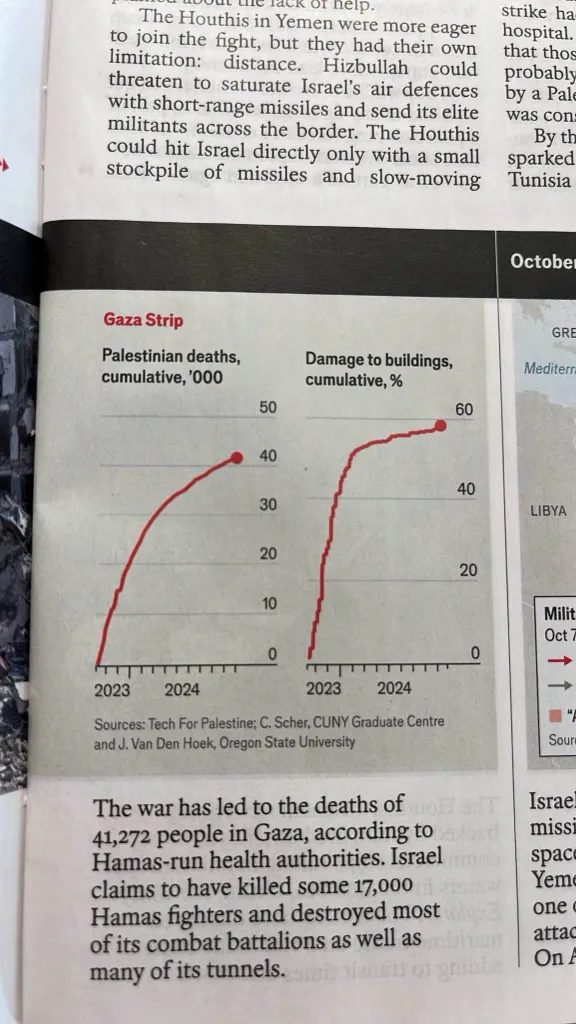
The killing according to the Gaza Ministry of Health statistics seems to be slowing down, but this is because the MoH is maintaining a very high bar for recording the deaths. The attacks on the population is continuing at what seems to be the same rate.
from: https://www.dropsitenews.com/p/how-gaza-health-ministry-counts-dead "The Ministry of Health is committed to registering only those who reach its hospitals or other emergency medical care facilities in the Gaza Strip. Consequently, the number of martyrs announced by the ministry does not necessarily represent the total number of casualties but only those that have been officially documented."
Given that state of the hospitals is dire (they have all been bombed and attacked), the slow down in recording of deaths correlates with and is due to the destruction of the MoH and general civilian infrastructure. The reduction in rate of killing recorded does not align with the rate of actual killing.
Also, have you ever wondered why South Africa of all countries brought the case to the ICJ? Probably because they are deeply offended by the Israeli apartheid and they are even more against genocide?
Do you think it has anything to do with the fact that they entertained Hamas leaders as visiting dignitaries a month before they submitted the case? Um, yes. Why would they not do this?
Ah, you classify Hamas as a terrorist organisation.... Since South Africa regards Hamas to be a resistance movement (and this is the position of most of the world), coordinating with them would be sensible.
Sir, your president is quoted in the genocide case (South Africa vs Israel) as one of the inciters to genocide.
I wonder why Israel does not allow journalists into Gaza and has killed more than 170 Palestinian journalists?
See Brexit. That was to leave but same principle.
Are you actually saying that Sinwar's strategy paid off?
No, it would be war squared.
Or maybe war(war());
This is sort of report you get from a reporter under military censorship.
What sort of army does not fight against an invading force? Is this why Hezbollah exists?
Sending out IEDs that will probably explode in a supermarket and kill civilians is generally considered a war crime. So far 2 kids killed in Beirut by the Israeli bombs in devices.
The 40,000 killed statistic is reliable in that the killed persons name, identity number etc are reported to MoH officials and recorded by them, and the dead are seen by the officials. However the figure is a small subset of the actual number dead. 200,000 to 300,000 dead in Gaza in the past year is a conservative estimate.