this post was submitted on 16 Jul 2023
0 points (NaN% liked)
Cybersecurity
5677 readers
107 users here now
c/cybersecurity is a community centered on the cybersecurity and information security profession. You can come here to discuss news, post something interesting, or just chat with others.
THE RULES
Instance Rules
- Be respectful. Everyone should feel welcome here.
- No bigotry - including racism, sexism, ableism, homophobia, transphobia, or xenophobia.
- No Ads / Spamming.
- No pornography.
Community Rules
- Idk, keep it semi-professional?
- Nothing illegal. We're all ethical here.
- Rules will be added/redefined as necessary.
If you ask someone to hack your "friends" socials you're just going to get banned so don't do that.
Learn about hacking
Other security-related communities !databreaches@lemmy.zip !netsec@lemmy.world !cybersecurity@lemmy.capebreton.social !securitynews@infosec.pub !netsec@links.hackliberty.org !cybersecurity@infosec.pub !pulse_of_truth@infosec.pub
Notable mention to !cybersecuritymemes@lemmy.world
founded 1 year ago
MODERATORS
you are viewing a single comment's thread
view the rest of the comments
view the rest of the comments
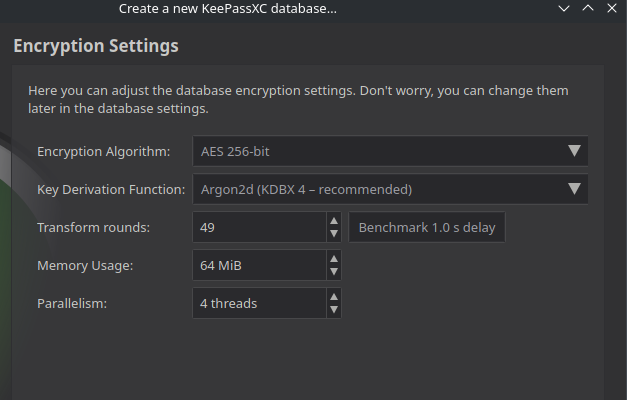
Those last three input boxes are all parameters to fine tune the operation of the key derivation function, they control the performance and hardware usage characteristics of how to derive the actual database encryption key from your password in order to make it harder to brute force.
The Transform Rounds input essentially controls how much sequential processing power is needed by repeating a specific part of the KDF more or less often, and thus allows you to determine how long the key derivation will take every time. That's why there's a Benchmark button next to it - it will automatically test on your CPU and determine how many rounds are needed to produce a 1 second delay on your hardware. Which is an acceptable time to wait for your database to unlock, but bad news for someone trying to brute force your password, as it limits how many different passwords they can test in a given time.
Memory usage controls the amount of memory the KDF needs, and Parallelism controls how many parallel threads are used, both limiting how many parallel attempts at brute forcing your password a potential attacker can run on any given hardware.
Disclaimer: I'm not a security expert, just a software developer who has come into contact with KDFs quite a bit. If I misrepresented anything above, happy for correction!