DOI
https://matrix.to/#/#donoperinfo:matrix.org
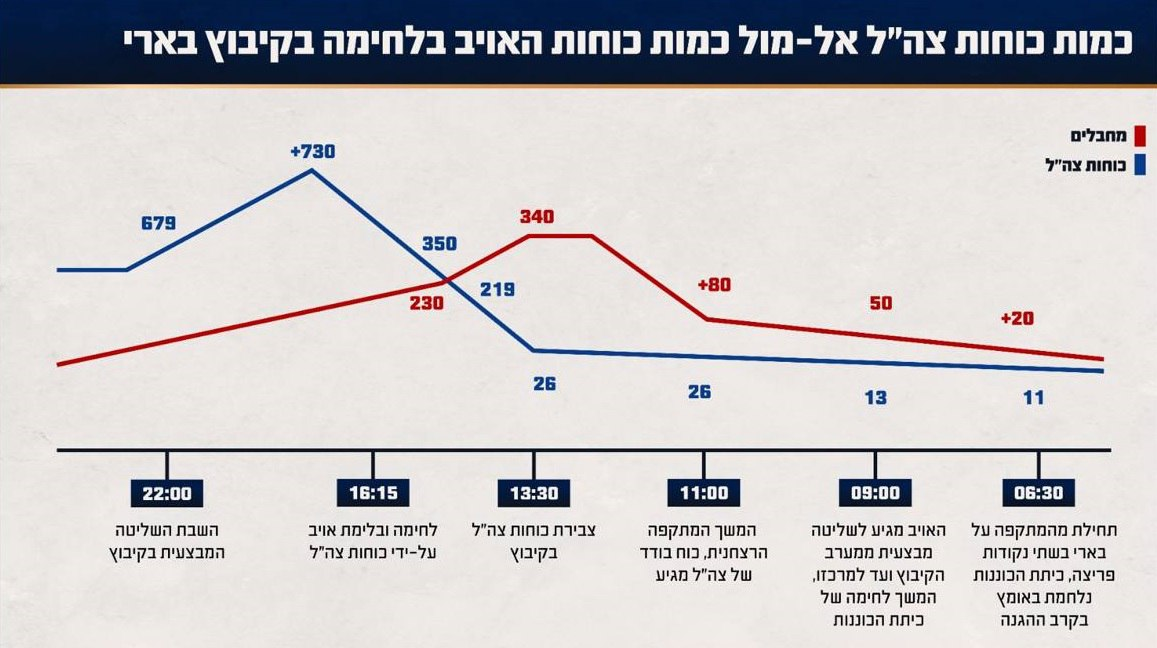
Установлено, что когда начался бой, в 6:30 утра, против нескольких десятков боевиков, которые были авангардом более крупных сил, стояли только чуть более десяти самооборонцев кибуца. Они храбро сражались, но силы атакующих боевиков стремительно росли.
Только в 11:00 утра прибывает небольшой отряд израильской армии размером с отделение и вступает в бой. Боевиков же уже сотня, и на пике в 13:30 их становится до 340 против 26 израильских самооборонцев и солдат. По факту батальон против взвода. Боевики жгут кибуц, убивают, насилуют и похищают людей.
Только после 13:30 начинают прибывать существенные силы армии, которые в ходе боев возвращают контроль над кибуцем и к 22:00 вечера стабилизируют обстановку. В ходе резни в Беэри были убиты 101 гражданский, и еще 30 были похищены. Также в бою пали 5 самооборонцев, 18 солдат АОИ и 8 сотрудников полиции. Боевиков было уничтожено более 100, остальные отошли обратно в сектор Газа вместе с захваченными гражданами.
Армия делает вывод из этого расследования, что она провалила свою миссию по защите жителей кибуца, а храбрость самооборонцев достойна чести, и именно они, будучи в подавляющем меньшинстве, но навязав бой, сдержали атаку и не дали боевикам добраться до других частей кибуца.
Нужно отметить, что это только первичный вывод из серии расследований и касается только конкретного кибуца. Но даже эти первичные выводы из страшных событий 7 октября снова подсвечивают верность мысли, которую иллюстрирует нам российско-украинская война: тезис, что лучший бьет многих, оказался ошибочным.
Масса решает, и у взвода, пусть даже самых храбрых бойцов, крайне мало шансов против батальона мотивированных и вышколенных боевиков.
@yigal_levin
информация про последствия обстрела разлетелась с молниеносной скоростью от низов то верхов и наоборот
очень много снарядов, дронов и прочего с разными надписями будет летать все последующие дни на головы руснявым недобойцам на передке и в тылу
мотивации хуярить этих пидаров сегодня конечно добавилось максимально
есть один минус - скорее всего в последующие дни в плен будут брать меньше руснявых, особенно тех, кто не выполняет прямые указы украинского солдата при сдаче в плен
но то такое
неприятность эту мы переживем
CNN: российские власти готовили покушение на главу Rheinmetall. Эта компания производит оружие — в том числе для Украины — Meduza https://meduza.io/news/2024/07/11/cnn-rossiyskie-vlasti-gotovili-pokushenie-na-glavu-rheinmetall-eta-kompaniya-proizvodit-oruzhie-v-tom-chisle-dlya-ukrainy
Російські Власти Готували Замах на Главу Rheinmetall: Аналіз та Прогноз
Вступ
11 липня 2024 року видання Meduza, посилаючись на CNN, повідомило про спробу покушення на главу німецької оборонної компанії Rheinmetall. Ця компанія відома виробництвом зброї, зокрема для України. Інцидент привернув увагу міжнародної спільноти, висвітливши питання безпеки та політичних напружень у контексті російсько-українського конфлікту.
Основний текст
Rheinmetall, провідний німецький виробник оборонної техніки, став мішенню для російських спецслужб. Компанія постачає зброю до багатьох країн світу, включаючи Україну, що викликає значну напруженість у відносинах з Росією. За даними CNN, російські власті ретельно готували атаку на генерального директора Rheinmetall, щоб підірвати його діяльність та зупинити постачання зброї.
Аналіз ситуації
-
Мотиви та цілі Росії:
- Стратегічний інтерес: Послаблення одного з ключових постачальників зброї для України могло б суттєво вплинути на оборонні спроможності цієї країни.
- Психологічний ефект: Така атака могла б мати значний психологічний вплив, створюючи атмосферу страху та невизначеності серед керівників західних оборонних компаній.
-
Наслідки для міжнародних відносин:
- Погіршення відносин між Росією та Заходом: Цей інцидент може призвести до нових санкцій та ще більшого загострення конфлікту між Росією та країнами НАТО.
- Зростання підтримки України: Західні країни можуть збільшити підтримку України, бачачи необхідність у посиленні її обороноздатності.
-
Відповідь Rheinmetall та Німеччини:
- Підвищення безпеки: Після цього інциденту Rheinmetall та інші оборонні компанії, ймовірно, посилять свої заходи безпеки.
- Політичні кроки: Німецький уряд може посилити заходи щодо захисту критично важливих галузей економіки від іноземних загроз.
Висновок
Інформація про спробу покушення на главу Rheinmetall свідчить про високий рівень напруженості у міжнародних відносинах та готовність Росії діяти агресивно для досягнення своїх цілей. Цей інцидент може мати далекосяжні наслідки для європейської безпеки та стабільності. Він також підкреслює необхідність посилення міжнародної співпраці у сфері безпеки та розвідки.
Прогноз
- Посилення міжнародної напруженості: Відносини між Росією та країнами Заходу, ймовірно, ще більше загостряться.
- Збільшення підтримки України: Західні країни можуть збільшити фінансову та військову допомогу Україні.
- Підвищення безпеки в оборонному секторі: Оборонні компанії та уряди посилять заходи безпеки для захисту від можливих атак.
Гештеги
#Rheinmetall #Безпека #МіжнароднаПолітика #Україна #Росія #Оборона #Конфлікт #Покушення
Цей аналіз допоможе зрозуміти ситуацію навколо спроби покушення на главу Rheinmetall та її потенційні наслідки для міжнародної політики та безпеки.
Qoto Mastodon https://qoto.org/web/statuses/112771085768176865

(1) Oles Filonenko 🤷🏼♂️ on X: "Когда тебя дома не покормили https://t.co/fuGg50xvDQ" / X https://x.com/FilonenkoOles/status/1811059122667692045
Вспомнил видео снятое финами на даче где Путин играет в теннис и жрет за столом с Анатолием Собчак. Очень много схожего. Так что вполне вероятно это и есть настоящий Путин, но только где страх и осторожность отравления при таком огромном количестве людей вокруг? 🤔
https://bastyon.com/internews112?ref=PMC55eKCrsxoJNkiB3f71AgFLQC3T9HkWV
DW3 min View Original 06.07.2024July 6, 2024 The "Ukrainian group" was already developing plans to blow up gas pipelines in 2014, after Russia's annexation of Crimea, Welt am Sonntag writes, citing intelligence data.
The destruction of the Nord Stream and Nord Stream 2 gas pipelines was planned much earlier than the start of the full-scale Russian military invasion of Ukraine , namely back in 2014, after Russia annexed the Ukrainian peninsula of Crimea. This was reported on Saturday, July 6, by the newspaper Welt am Sonntag, citing data from German and international investigations, as well as intelligence services, which the editorial board obtained.
It is indicated that the corresponding plans could have been developed at that time by a certain "Ukrainian group". "If the existence of long-term plans (to destroy the SP and SP-2 gas pipelines - Ed. ) on the part of the Ukrainian state is proven, this could have the most serious impact on the Germans' desire to support the Ukrainians," the publication says.
By 2014, the Nord Stream gas pipeline had already been in operation for two years, and the construction of Nord Stream 2 was at the planning stage, the authors recall.
Explosions at Nord Stream On September 26, 2022, the SP and SP-2 pipes were damaged as a result of underwater explosions recorded near the Danish island of Bornholm. The motive for this crime, as well as its perpetrator, are still unknown. Denmark and Sweden have closed their national investigations into the explosions. However, in Germany, the Federal Police and the Federal Criminal Office, on behalf of the Federal Prosecutor's Office, continue to work on this case , which is regarded as an act of sabotage . "The investigation is ongoing," the Welt am Sonntag newspaper quotes the Federal Prosecutor's Office of Germany as saying in this regard.
The central focus of the German investigation is the sailing yacht Andromeda, which was rented in the federal state of Mecklenburg-Vorpommern at the time of the explosions. As a German official familiar with the investigation told journalists on condition of anonymity, new indications have recently emerged that six people on board the yacht may have been involved in the gas pipeline explosions.
Doubts about Ukraine's involvement However, the intelligence services have doubts about this. Thus, Gerhard Schindler, who headed the German intelligence service BND from 2011 to 2016, said in an interview with Welt am Sonntag: "The results of the investigation may lead to a Ukrainian group. But this does not mean that Ukraine was the customer . From the point of view of the intelligence services, many things indicate that this could have been a Russian operation under a false flag. They have such capabilities." As for the traces that lead to Ukraine, according to Schindler, they could have been left intentionally.
Immediately after the version about Andromeda's involvement in the Nord Stream explosions appeared in March 2023, the German tabloid Bild wrote about experts' serious doubts about its plausibility.
Journalists found out, in particular, that Andromeda, apparently, is too small to be used for such a large-scale sabotage. In addition, it is not equipped with special diving equipment that would allow explosives to be planted at a depth of 80 meters.
"To carry out three explosions underwater would require at least 600 to 900 kg of special military explosives. The yacht Andromeda does not have a crane to safely lower such a volume underwater," the publication emphasized.
Data from Polish intelligence services As Welt am Sonntag writes, Polish politicians and intelligence services also have doubts about Ukraine's involvement in the explosions at Nord Stream. In the summer of 2023, Polish intelligence services handed over to the BND a list of people who, according to their information, were connected to the terrorist attack on the pipelines and, as is assumed, had contacts with Moscow.
Polish intelligence services also claimed that the "Ukrainians" who rented the yacht "Andromeda" using fake passports were in fact Russian citizens. They deliberately left a false trail to discredit Ukraine, they believe in Poland.
(2) ✙ Alterego (Midshipman) ✙ в X: «✙ Alterego (Midshipman) ✙ в Elk: "https://t.co/6rC0xSDedf..." | Elk https://t.co/lKpcLhLuJx» / X https://x.com/CASBT_OSINT_UA/status/1809690932872376657
Netbird - це інструмент, який дозволяє безпечно з'єднувати кілька пристроїв у єдину приватну мережу за допомогою технології WireGuard®. Він спрощує керування доступом за допомогою функцій, таких як єдиний вхід (SSO) і багатофакторна аутентифікація (MFA). Це створює безпечну, легку у використанні мережу, де ви можете контролювати доступ і забезпечувати безпеку ваших пристроїв. Більше інформації можна знайти на їх GitHub сторінці.
christianwol-ff/netbird: Connect your devices into a single secure private WireGuard®-based mesh network with SSO/MFA and simple access controls. https://github.com/christianwol-ff/netbird
Він спрощує керування доступом за допомогою функцій, таких як єдиний вхід (SSO) і багатофакторна аутентифікація (MFA). Це створює безпечну, легку у використанні мережу, де ви можете контролювати доступ і забезпечувати безпеку ваших пристроїв. Більше інформації можна знайти на їх GitHub сторінці.
Netbird допомагає об'єднати ваші пристрої у захищену мережу, як ніби вони всі підключені до одного Wi-Fi, навіть якщо вони знаходяться в різних місцях.
Приклади та аналогії:
- VPN для вашої особистої мережі: Як особистий VPN, але для всіх ваших пристроїв, щоб вони могли "спілкуватися" між собою безпечно.
- Сім'я на відстані: Уявіть, що у вас є комп'ютери вдома, на роботі та у друга. Netbird дозволяє їм бути у одній безпечній мережі, як ніби всі вони вдома.
Прості слова:
- З'єднує пристрої: Всі ваші пристрої можуть "бачити" один одного, як якщо б вони були підключені до одного Wi-Fi.
- Безпечно: Захищає вашу мережу від сторонніх.
- Легке керування: Просте налаштування і контроль доступу до вашої мережі.
Приклад використання:
- Віддалена робота: Ви можете отримати доступ до домашнього комп'ютера з роботи.
- Спільні ігри: Друзі можуть грати разом в одній мережі, навіть якщо вони знаходяться в різних місцях.
Title: Netbird: Simplifying Secure Device Connections
Annotation:
Netbird allows users to securely connect multiple devices into a single private network using WireGuard® technology. It simplifies access control through Single Sign-On (SSO) and Multi-Factor Authentication (MFA), creating an efficient and easy-to-manage mesh network.
Keywords:
Netbird, secure network, WireGuard, SSO, MFA, private network, device connectivity, mesh network, network security, access control, decentralized networking, IT infrastructure, remote access.
Analytical Report and Forecast:
Netbird is positioned to transform the way devices connect and communicate securely. By utilizing WireGuard® technology, it provides a robust solution for creating private mesh networks that are both secure and easy to manage. Key features like Single Sign-On (SSO) and Multi-Factor Authentication (MFA) enhance security and streamline access control, making it an attractive option for both individuals and businesses. As the demand for secure, decentralized networking solutions grows, Netbird is likely to see increased adoption across various sectors, particularly those requiring secure remote access and efficient IT infrastructure management.
Hashtags:
#Netbird #SecureNetwork #WireGuard #SSO #MFA #PrivateNetwork #DeviceConnectivity #MeshNetwork #NetworkSecurity #AccessControl #DecentralizedNetworking #RemoteAccess #ITInfrastructure #TechInnovation #CyberSecurity #DigitalTransformation #NetworkManagement #SecureCommunication #TechSolutions #ITSecurity #NetworkingTechnology #DigitalNetworking #ITSupport
Editorial Comment:
Netbird's innovative use of WireGuard® technology to create secure, manageable private networks addresses a critical need in today's increasingly digital and decentralized world. By offering seamless access control and robust security features, Netbird is set to become a go-to solution for both personal and professional networking needs. Its user-friendly approach to complex networking challenges makes it an invaluable tool for enhancing security and connectivity in a variety of settings.
Conclusion, Keywords, Links:
Netbird, secure network, WireGuard, SSO, MFA, private network, device connectivity, mesh network, network security, access control, decentralized networking, IT infrastructure, remote access.
Description for Google search robots (150 characters):
Netbird securely connects devices in a private network using WireGuard, with easy access control via SSO and MFA, enhancing security and manageability.
Peer2Pool - це децентралізована платформа для майнінгу криптовалют, яка об'єднує ресурси від індивідуальних користувачів, дозволяючи їм спільно майнити та розподіляти нагороди. Платформа забезпечує прозорість і справедливий розподіл винагороди завдяки використанню блокчейн-технологій, усуваючи необхідність довіряти центральному органу. Peer2Pool дозволяє майнерам ефективно використовувати свої ресурси та отримувати більші доходи в порівнянні з індивідуальним майнінгом.
Більше інформації можна знайти на офіційній сторінці Peer2Pool або відповідних криптовалютних форумах.
Title: Peer2Pool: Revolutionizing Cryptocurrency Mining
Annotation:
Peer2Pool is a decentralized platform that revolutionizes cryptocurrency mining by pooling resources from individual users, ensuring transparency and fair distribution of rewards using blockchain technology. This method enhances efficiency and increases revenue compared to traditional individual mining approaches.
Keywords:
Peer2Pool, decentralized mining, cryptocurrency, blockchain, mining pool, transparency, fair distribution, resource efficiency, increased revenue, blockchain technology, cryptocurrency mining, mining rewards, individual miners.
Analytical Report and Forecast:
Peer2Pool represents a significant advancement in cryptocurrency mining by leveraging blockchain technology to pool resources from multiple users. This decentralized approach not only ensures transparency but also promotes fair distribution of mining rewards. By eliminating the need for a central authority, Peer2Pool enhances trust and security among its users. The platform's ability to efficiently utilize resources results in higher revenue for miners compared to individual efforts. As blockchain technology continues to evolve, Peer2Pool is poised to become a key player in the cryptocurrency mining landscape, attracting more miners seeking efficient and transparent mining solutions.
Hashtags:
#Peer2Pool #DecentralizedMining #Cryptocurrency #Blockchain #MiningPool #Transparency #FairDistribution #ResourceEfficiency #IncreasedRevenue #BlockchainTechnology #CryptoMining #MiningRewards #IndividualMiners #CryptoRevolution #DigitalCurrency #BlockchainInnovation #MiningCommunity #CryptoFuture #DecentralizedFinance #BlockchainEcosystem
Editorial Comment:
Peer2Pool's innovative approach to cryptocurrency mining is a game-changer, addressing many of the inefficiencies and trust issues associated with traditional mining methods. By pooling resources and ensuring transparent reward distribution, Peer2Pool not only enhances profitability for miners but also strengthens the overall integrity of the mining process. As the cryptocurrency market continues to grow, platforms like Peer2Pool are essential in fostering a more efficient and secure mining ecosystem.
Conclusion, Keywords, Links:
Peer2Pool, decentralized mining, cryptocurrency, blockchain, mining pool, transparency, fair distribution, resource efficiency, increased revenue, blockchain technology, cryptocurrency mining, mining rewards, individual miners.
Description for Google search robots (150 characters):
Peer2Pool is a decentralized platform that pools resources for efficient, transparent cryptocurrency mining, ensuring fair reward distribution via blockchain technology.
(33) ### Title: Peer2Pool: Revolutionizing Cryptocurrency Mining https://ecency.com/hive-181335/@murchandiser/title-peer2pool-revolutionizing-cryptocurrency-mining
Вот список ТОП-10 криптопроектов, которые поддерживают стейкинг, с указанием их средней доходности (APY — годовая процентная доходность) на 2024 год. Обратите внимание, что доходность может изменяться в зависимости от множества факторов, включая рыночные условия и политики вознаграждений сети.
ТОП-10 криптопроектов для стейкинга по уровню доходности:
-
Polkadot (DOT)
- Средняя доходность: 13-15% APY
- Polkadot — мультичейновая сеть, которая соединяет различные блокчейны. DOT используется для стейкинга и обеспечения безопасности сети.
-
Solana (SOL)
- Средняя доходность: 6-8% APY
- Solana — высокопроизводительная блокчейн-платформа, поддерживающая смарт-контракты и децентрализованные приложения (dApps).
-
Cardano (ADA)
- Средняя доходность: 4-6% APY
- Cardano — блокчейн-платформа с открытым исходным кодом, ориентированная на обеспечение безопасности и масштабируемости.
-
Avalanche (AVAX)
- Средняя доходность: 8-10% APY
- Avalanche — платформа для создания и запуска децентрализованных приложений и блокчейн-решений.
-
Tezos (XTZ)
- Средняя доходность: 5-7% APY
- Tezos — блокчейн с механизмом самоуправления, поддерживающий смарт-контракты и формальные методы валидации.
-
Cosmos (ATOM)
- Средняя доходность: 7-10% APY
- Cosmos — сеть блокчейнов, направленная на обеспечение взаимодействия между различными блокчейнами.
-
Ethereum 2.0 (ETH)
- Средняя доходность: 4-6% APY
- Ethereum 2.0 — обновление сети Ethereum, переход на алгоритм консенсуса Proof-of-Stake (PoS).
-
NEAR Protocol (NEAR)
- Средняя доходность: 10-12% APY
- NEAR Protocol — платформа для децентрализованных приложений, использующая механизм шардинга для повышения масштабируемости.
-
Algorand (ALGO)
- Средняя доходность: 5-7% APY
- Algorand — блокчейн, ориентированный на решение трилеммы масштабируемости, безопасности и децентрализации.
-
Elrond (EGLD)
- Средняя доходность: 10-15% APY
- Elrond — платформа для децентрализованных приложений и корпоративного использования, предлагающая высокую производительность и безопасность.
Замечания:
- Изменчивость доходности: Уровни доходности могут значительно колебаться из-за изменений в сети, рыночных условиях и политике вознаграждений. Рекомендуется проверять актуальные ставки непосредственно в кошельках или на официальных сайтах проектов.
- Риски: Стейкинг, как и любые инвестиции, связан с рисками. Важно понимать возможные риски, такие как волатильность цен, технические проблемы и изменение политик сети.
Для актуальных данных и принятия решений по стейкингу рекомендуется использовать специализированные платформы, такие как StakingRewards, которые предоставляют актуальные ставки доходности и другую важную информацию о стейкинге.
ole.lukoile777 в Elk: "Стейкинг стал популярным способом пас..." | Elk https://elk.zone/zhub.link/@olelukoie/112603927805303911
В Вологде убита любительница чудесных «восточных сказок» и преподаватель ВоГУ Таисия Тулина.
Старший преподаватель кафедры всеобщей истории и социально-экономических дисциплин ВоГУ Таисия Тулина (36 лет), была обнаружена в квартире со своим сожителем, уроженцем Таджикистана и выпускником её ВУЗа Орифом Менглибоевым 28 лет). Он также был ранен и госпитализирован, т.к. его жертва пыталась оказать сопротивление.
Tomas Berezovskiy on X: "KARBO Project KdTRJpDnV1hjWFyqnar4jJZeGPLFFfGoo5UfRjef4yX75NsTvYJUpmo7cVozjpHcFf37Dn2L6uMwPDtYeWAvnLXiQwa4Tpc Украинский биткоин. Что представляет из себя отечественная криптовалюта / NV https://t.co/HUcRIdv7wM" / X https://x.com/internews112/status/1800474367736070349
https://internews112.blogspot.com/2024/06/ukrainian-bitcoin.html
Ukrainian Bitcoin. What is domestic cryptocurrency? biz.nv.ua5 min View Original Already today, cryptocurrencies make up almost 1% of the entire global money supply, which is a little less than $300 billion – and this figure is growing every day. This spring, the Ukrainian cryptocurrency Karbo was in the spotlight of famous American crypto resources. Having appeared just two years ago, Karbo entered the world ranking of the TOP 10 cryptocurrencies with increased anonymity by capitalization.
The majority of cryptographers and crypto traders surveyed by NV believe that Karbo has a high chance of gaining a foothold in the global market for anonymous transfers, since technically today it is not inferior to industry leaders - Monero, Dash and Zcash. According to bolder assumptions, in the future Karbo could become the national cryptocurrency of Ukraine. The absence of a premine (part of the emission that the developer keeps for himself) and the latest initiatives of advanced states to legalize certain cryptocurrencies as legal means of payment on their territory confirm these assessments.
NV figured out how things really stand with the domestic cryptocurrency Karbo.
What is Karbo and where did it come from? The Ukrainian cryptocurrency Karbo was created by a group of Ukrainian programmers and mathematicians, about which almost nothing is known, due to their desire to remain anonymous. The coin appeared directly on the market in May 2016. In professional terms, Karbo is a decentralized peer-to-peer peer-to-peer network that operates on the CryptoNote protocol and provides confidentiality and anonymity without intermediaries and regulators. Until recently, it remained an internal tool of enthusiasts on cryptocurrency exchanges, but this winter, American specialized analysts found it on the list of coins for which the US National Security Agency cannot yet track transactions , which is why it requires additional funding to continue work on cracking the code .
Thus, the United States noted one of the highest indicators of anonymity and security of Ukrainian cryptocurrency - its owners cannot be tracked in principle.
What is the point of investing in Karbo? In two years, the cost of Karbo has increased 86 times – from 0.058 to 0.5 cents, which is already a good reason to buy this particular cryptocurrency. Its main advantage is a unique computer algorithm, which during the transfer process creates dozens of one-time wallets, into which parts of a randomly divided payment are received, and only then the algorithm sends their amount to the recipient. All coins are standardized and do not have any identifying symbols.
By comparison, with Bitcoin, each transaction is stored in clear form on the blockchain, which makes it relatively easy to find out the balance, transaction history and sources of replenishment of your wallet. In Karbo, it is simply impossible to find such information even about very large transactions. Thirdly, the algorithm specifies the maximum number of coins - 10 million (currently 5.7 million have already been issued), after the release of which the issue volume will grow by only 1% per year.
How safe is it to use Karbo? According to technical characteristics, due to increased anonymity, Karbo belongs to the Bitcoin 2.0 family of cryptocurrencies. There are not many such cryptocurrencies; their main feature is complex encryption, to which no intelligence agency can find the key. Ukrainian regulation in the field of cryptocurrencies is very far from ideal, but neither the American nor the Ukrainian police will ever collect evidence of transactions with currencies operating on the CryptoNote protocol, including Karbo.
From a technical point of view, Karbo provides users with a completely anonymous payment scheme. It is implemented using ring signature technology, when the operation is confirmed not by each specific miner, but by a group of unrelated individuals. Such a signature only indicates that the transaction was carried out by someone from the group, but all participants in it are indistinguishable from each other. At the same time, Karbo retains all the advantages of the blockchain in the form of the impossibility of making the same payment twice or conducting a transaction without the network’s acceptance.
Karbo's ring signature technology uses a modified Diffie-Hellman exchange protocol that maps unique addresses to a public key. Each transaction made makes his blockchain as a whole even more resistant to analysis. But at the same time, Karbo allows, if necessary, reporting using tracking keys, which make it possible to see incoming transactions, but not outgoing ones, and also confiscate funds. Additionally, tracking keys do not reveal the sender.
Where do they sell and buy Karbo? Buying Karbo is no more difficult than buying any other cryptocurrency. Now Karbo can be purchased in online cryptocurrency exchangers, which will take up to 10 minutes, or on cryptocurrency exchanges, which, depending on whether you buy it for Bitcoin or hryvnia, can be a little more complicated and require registration on the exchange.
Karbo is currently traded on seven exchanges: Livecoin.net, Cryptopia, Crex24, TradeOgre, Altex.exchange, BTC Trade UA and Kuna. On the first five, it is traded in pairs with Bitcoin, and on BTC Trade UA and Kuna - Karbo can be sold and bought for hryvnia. It is the last two exchanges that are most convenient for use by newcomers in this area - integration with accounts in Ukrainian banks allows you to buy cryptocurrency just like cinema tickets or food.
The daily trading volume for Karbo on these exchanges is $20-30 thousand, and the total capitalization of the cryptocurrency is currently close to $3 million.
Cryptocurrency traders believe that there is no need to wait for the right moment to buy, because it is already happening. Advanced countries, whose policies the rest of the world is trying to implement, have almost mastered and legalized cryptocurrency transactions. Most recently, Switzerland allowed maintaining bank accounts in cryptocurrency; before that, this option was available in the banking systems of Japan, Singapore and South Korea. Although in many countries, including Ukraine, regulations for regulating the crypto industry are still in the process of development and approval. According to forecasts, 2018 will be the year of legalization of transactions with tokens in most countries of the world, including Ukraine. Since the adoption of digital decrees in the EU and other first world countries, cryptocurrency prices will rapidly creep up.
New, honest cryptocurrencies will continue to appear with no preliminary issue for developers and low commissions, but just as Bitcoin remains the most popular cryptocurrency because it was the first, so Karbo in Ukraine has every chance of becoming a local “bitcoin” as a pioneer in this market segment.
На дверь общежития белгородского вуза ко Дню России повесили флаг Нидерладов, — RusNews
Нидерландский флаг заметили на двери общежития Белгородского государственного аграрного университета.Рядом размещены российский флаг, белые голуби, надписи "Z — своих не бросаем" и "Временное укрытие".
Подробности: ▪Украина запустила минимум 10 ATACMS, ни одна ракета не была сбита. ▪Удары были нанесены по 31-й дивизии ПВО ВС РФ в трёх районах: Джанкойском, Сакском и Черноморском. ▪Джанкойский район: попали 4 ракеты, повреждены две РЛС. ▪Сакский район: попали 4 ракеты, повреждена военная техника, подробности уточняются. ▪Черноморский район: попали 2 ракеты, повреждены две РЛС и два комплекса С-300.
Они думают, что настоящая война — это когда с окопа вылазит солдат и с лопатой идет против танка. Война для них, это когда обе стороны закидывают друг друга «мясом», а вокруг огонь от подбитой техники. И вот только в такой картинке и только в таком виде происходит для них война. Нет, уважаемые, война сегодня очень далека от ваших представлений. С лопатой на танк идет только идиот. Нормальный человек отступает. И это НОРМАЛЬНО. «Мясом» закидывать противника может только деспот и тиран. Нормальный главнокомандующий делает все, чтобы сохранить жизнь каждого солдата. Все от слова СОВСЕМ ВСЕ. Ваша картинка с окопами, трупами и горящими танками — это крайний случай боевых действий. А сами боевые действия — всего лишь третья часть от войны. БольшАя часть войны сегодня происходит на поле боя дипломатии. Это поле менее страшно по виду, но более драматично по чувствам. Ты не можешь на нем поддаться эмоциям, зажать курок автомата и с криками «здохните @дарасы» выпустить магазин патронов. На нем ты должен держаться, погашать все эмоции, чтобы рассудок оставался трезв. Ты должен там переступать через себя, жать руку врагу, улыбаться и приветливо кивать. Твоя цель — это ослабить врага, запутать его, обмануть, если хотите, и в нужный момент вставить фразу, которая ударит по нему больнее сотни залпов «Града». На этом поле ты вынужден жертвовать малым, чтобы добиться или спасти бОльшее. И хорошо, если ты жертвуешь чем то своим личным. Тогда тебе никто не предъявит претензий и некому будет сложно смотреть в глаза. Гораздо хуже, когда такие жертвы касаются не твоего личного... Практически все решения принятые на поле боя дипломатии никогда бы не принял кто то из вас. Так же, как и никто из вас не продержался бы там столько, сколько держатся дипломаты. Поэтому, наверное, вы даже не хотите воспринимать существование такого «поля боя» и правил ведения войны на нем. Это поле вам непонятно, но оно есть. И там такие вот правила ведения войны.
10-06-2020
The posters are no longer needed, Andrei is no longer a hostage. He was released by IDF soldiers. The Russian authorities, of course, have long forgotten about their citizen.
The Russian authorities have not only forgotten about their citizen hostage, but have also been "sticking their necks out" to the Israeli authorities, actually preventing his release.
(1) OSINT_Alfa в X: «В Израиле снимают плакаты о заложнике Хамаса россиянине Андрее Козлове. Плакаты больше не нужны, Андрей больше не заложник. Его освободили солдаты ЦАХАЛ. Российские власти о своём гражданине, разумеется, давно забыли. https://t.co/FFwveK2AjF» / X https://x.com/OSINT_Alfa/status/1799704414170595679

Information Anonymous gate to I2P, TOR, Yggdrasil and clearnet. If the statistics on this page scare you, read the source code - the server does not store addresses from which requests come.
Proxy server accessible from I2P:
proxy4uwdijqxac2bvdx4fuhem6njmiwukuk2gelejv2nzxka2xq.b32.i2p outproxy.acetone.i2p ...and Yggdrasil:
[324:71e:281a:9ed3::fa11] outproxy.acetone.ygg (alfis)
SOCKS port: 1080
HTTP port: 3128
Instructions for i2pd users: HTTP and SOCKS.
You can help pay for servers by donating monero.
кросс-пост из: https://sopuli.xyz/post/5048225
Original:
Source: https://t.me/pravdaGerashchenko_en/28697
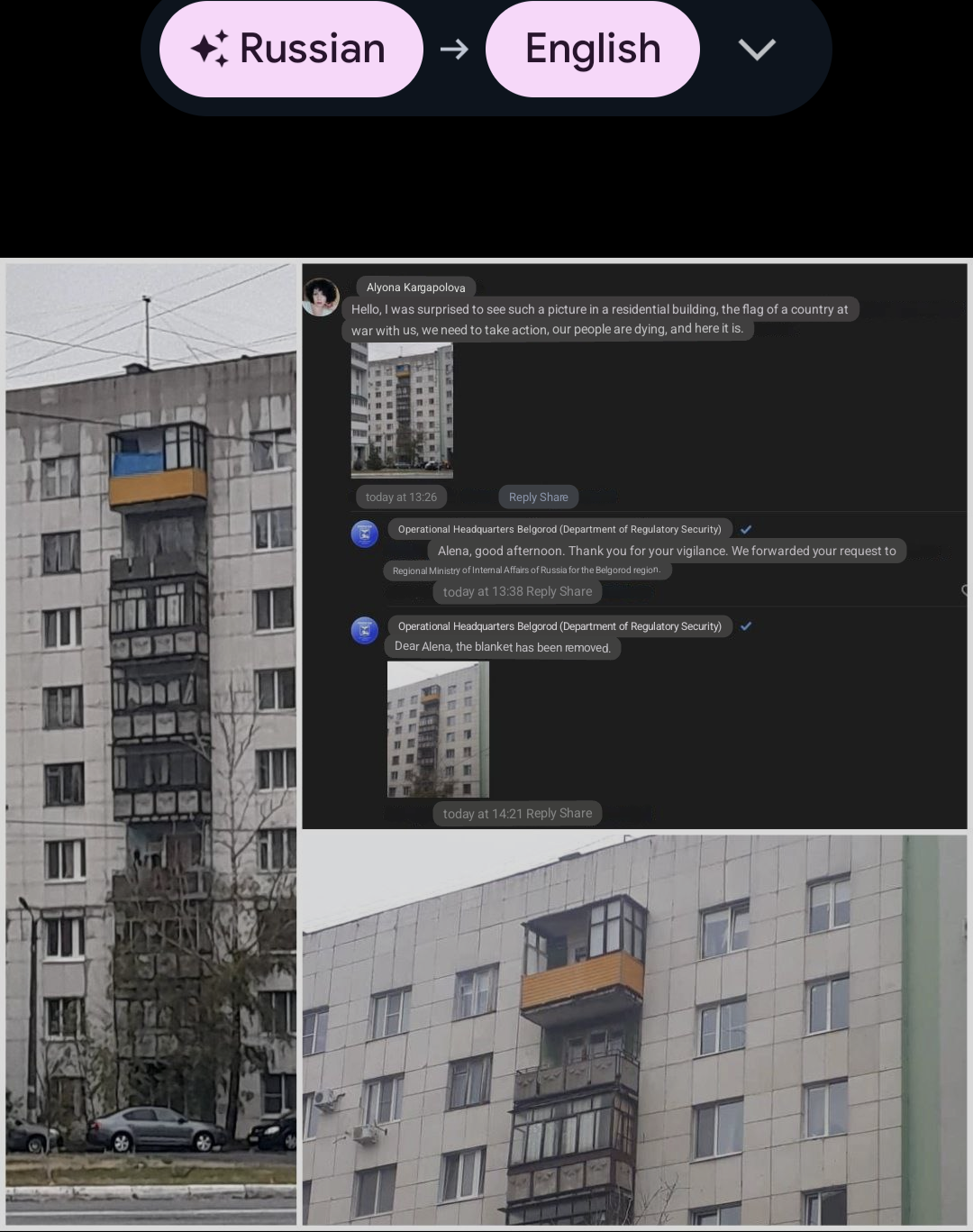
In Russian Belgorod, a woman reported a blue blanket on a yellow balcony to the local security department. She wrote that "measures need to be taken".
Shortly after, she received thanks for her vigilance and a report that the blanket was taken down, accompanied by a photo.
Russian paranoia is blooming.
Having made its first loss in 25 years and its all-time record loss, Gazprom is starting to sell off its property.
On Wednesday, the company announced (https://t.me/gazprom/1547) that it was looking for buyers for large real estate properties in Moscow and the Moscow region. Among them are office buildings on Stroiteley Street, the Imperial Park Hotel & Spa resort complex in Pervomayskoye settlement, Rogozino village, non-residential premises on the first floor of a house on Novocheremushkinskaya Street, as well as a 96-space parking lot near the company's headquarters in Moscow.
The decision was made "taking into account the completion of the relocation of Gazprom Group companies to St. Petersburg," the company's press service explained.
Last year Gazprom made a net loss of 629 billion rubles under IFRS, reported a 27% drop in revenue and a halving of EBITDA. The gas business of the company, which operates the largest reserves on the planet, became unprofitable (by 1.2 trillion rubles for the year), and Gazprom's debt reached a record 6.65 trillion rubles, exceeding the size of the liquid part of the National Welfare Fund (5 trillion rubles).
Subscribe (https://t.me/+aLbskvU4PBZhYTY6) / Read more (https://storage.googleapis.com/rdrct/mt.html#/2024/05/08/gazprom-nachal-rasprodavat-imuschestvo-posle-rekordnogo-vistorii-ubitka-a130237)
cross-posted from: https://lemmy.world/post/12898084
French President Emmanuel Macron met with parliamentary parties on Thursday. During the meeting Macron said he was open to the possibility of sending troops to Ukraine, as announced by, according to French newspaper L’Independant.
Fabien Roussel, a representative of the French Communist Party, said after the meeting that “Macron referenced a scenario that could lead to intervention [of French troops]: the advancement of the front towards Odesa or Kyiv.”
He noted that the French President showed parliamentarians maps of the possible directions of strikes by Russian troops in Ukraine.
Following the meeting, Jordan Bardella of the far-right National Rally party noted that “there are no restrictions and no red lines” in Macron’s approach.
Расширенное руководство по верификации видеоматериалов - Беллингкэт https://ru.bellingcat.com/materialy/putevoditeli/2017/07/18/advanced-video-verification-guide/
Aric Toler13-16 minutes 30.06.2017 One of the most common issues for researchers and journalists is verifying user-generated video content, most often found on social networks and file sharing platforms, such as YouTube, Twitter, Facebook, and so on. There is no silver bullet to verify every video, and it may be nearly impossible to verify some videos short of acquiring the original file from the source. However, there is a range of methods we can use to verify most content, especially as it relates to making sure that videos showing breaking news events are not recycled from previous incidents. There are already numerous guides online for verifying video, most notably in the Verification Handbook. This guide will include some extra quirks frequently used by the Bellingcat team, and make an effort to provide our readers with ways to work around the limitations of the available tools. After reading this guide, hopefully you will not only know how to use this tool set, but also how to use creativity in avoiding dead ends.
Flawed, but still useful: reverse image search The first step in verifying video content is the same as verifying images – run a reverse image search through Google or other services, such as TinEye. Currently, there are no freely available tools that allow you to reverse search an entire video clip the same way we can with image files, but we can do the next best thing by reverse image searching thumbnails and screenshots. People who create fake videos are rarely very creative, and will most often reshare an easy-to-find video without any obvious signs that it does not fit the incident, such as a news chyron or an audio track with someone speaking a language that does not fit the new incident. Because of this, it is relatively easy to fact-check recycled videos.
There are two ways to conduct this search. The first is to manually take screenshots of the video, best either at the very beginning or during key moments in the clip, and then upload them onto a reverse image search service, such as Google Images. The second is to rely on the thumbnails generated by the video host, most often YouTube. There is no easy way to determine which frame a video will automatically select as a thumbnail, as Google developed a complex algorithm for YouTube to select the best thumbnail for an uploaded video (for more on this, see the Google Research Blog entry on the topic here). Perhaps the best tool to find these thumbnails is Amnesty International’s YouTube DataViewer, which generates the thumbnails used by a video on YouTube and allows you to conduct a reverse image search on them in one click.
For example, a YouTube aggregator called Action Tube recently posted a video supposedly showing a convoy of military equipment in Lithuania, but without providing any source material for it. Additionally, there are no indications when the video was filmed, meaning that it could have been from yesterday or five years ago.
https://www.youtube.com/watch?v=zX7gu_gS3zE
If we search for this video on the Amnesty International tool, we find out the exact date and time that Action Tube uploaded the video, along with four thumbnails to reverse search to find the original source of the video.
None of the results give us a direct hit on the original source; however, a number of the results on the third thumbnail point to videos that showed this thumbnail on the page at one time. If you click these videos, you may not find this thumbnail, as the results for the “Up next” videos on the right side of a YouTube page are tailored for each user. However, the video with that thumbnail was present at the time when Google saved the results, meaning that you can find this video on the cached page.
Again, none of these five results are the source of the video we are looking for, but when Google cached away its snapshot of the page, the thumbnail video for the source was present on these videos’ pages. When we viewed the cached page for the first result above, we see the source for the video posted by Action Tube, with the title “Enhanced Forward Presence Battle Group Poland Conducts a Road March to Rukla, Lithuania.”
We now have all the information we need to track down the original video and verify that the Action Tube video does indeed show a recent deployment of military equipment in Lithuania. After we search the title of the video found in the thumbnail search result, we find six uploads. If we sort them by date, we can find the oldest upload, which served as the source material for Action Tube.
This leads us to a video uploaded on June 18, 2017 – a day before the Action Tube video, of June 19 – uploaded by “Maj Anthony Clas.” This is the same video shared by Action Tube.
https://www.youtube.com/watch?v=_4kHuTs1Nog
If we do a simple search on the uploader, we see that he has written articles for the U.S. Army website about NATO activities in Europe, meaning that he is likely a communications official, thus lending additional credence to his upload being the original source for Action Tube.
Creativity still more powerful than algorithms While reverse image searching can unearth many fake videos, it is not a perfect solution. For example, the video below, which has over 45,000 views, supposedly shows fighting between Ukrainian soldiers and Russian-backed separatist forces near Svitlodarsk in eastern Ukraine. The title translates to “Battle in the area of the Svitlodarsk Bulge in the Donbas (shot from the perspective of the Ukrainian Armed Forces).” We can see a lot of gunfire and artillery shots, while the soldiers seem to be laughing along with the fighting.
When we enter the video’s URL into Amnesty International’s tool, we see the exact date and time it was uploaded, along with thumbnails that we can reverse search.
When looking through the results, almost all of them are for around the same time that the video was uploaded, giving the appearance that the video could genuinely show fighting near Svitlodarsk in December 2016.
However, the video is actually from a Russian military training exercise from 2012.
Even with the most creative uses of reverse Google image search and using Amnesty International’s tool, you will not find this original video in the results, except in articles describing the debunking after the fake videos were spread. For example, if we search the exact title of the original video (“кавказ 2012 учения ночь,” meaning “Kavkaz 2012 night training,” referring to the Kavkaz 2012 military exercises), along with a screenshot from the video, we only find results for the fake Svitlodarsk video. Knowing that this video was fake required one of two things: a familiarity with the original video, or a keen eye (or ear) telling you that the laughing soldier did not correspond with the supposed battle taking place.
So, what is to be done? There is no easy answer, other than searching creatively. One of the best ways to do this is to try thinking like the person who shared a potentially fake video. With the example above, the laughing soldier gives you a clue that perhaps this is not real fighting, leading to a question of under what circumstances a Russian-speaking soldier would be filming this incident and laughing. If you wanted to find a video like this, what would you search for? You would want a video at night probably, so that there would be fewer identifiable details. You would also try looking through footage of spectacular looking fighting, but not something easily recognizable to Ukrainians or Russians following the war in the Donbas — so, finding videos of exercises from the Russian, Ukrainian, or Belarusian army could fit the bill, unless you found war footage from another country and overdubbed it with Russian speakers. If you search the Russian phrases for “training exercises” and “night,” this video would be the very first result. If you were not able to stumble your way to the original video, the best way to verify this video would have been to contact the person who uploaded it.
Be a Digital Sherlock with an eye for detail Using digital tools to verify materials is inherently limited, as algorithms can be fooled. Often, people use simple tricks to avoid detection from reverse image searches – mirroring a video, changing the color scheme to black and white, zooming in or out, and so on. The best way to overcome these factors is an eye for detail so that you can verify individual details in a video to make sure that the surroundings of the video is consistent with the incident at hand.
On September 19, 2016, reports came in that the m an responsible for three bomb explosions in New York City and New Jersey was arrested in Linden, New Jersey. A few photographs and videos emerged from different sources, including the two below showing the suspect, Ahmad Khan Rahami, on the ground surrounded by police officers.
The exact address in Linden, NJ where he was arrested was not clear, but it was a safe bet that these two photographs were real, considering how they showed roughly the same scene from two perspectives. The video embedded below also emerged, from a local citizen. Clearly, the video is real, as it was shared widely on news outlets throughout the day, but how could we have done lightning-fast verification to know it was real in the middle of the breaking news situation?
We can figure out where Rahami was arrested quite quickly from the two photographs. In the bottom-left corner of the second photograph, we can see an advertisement with four numbers (8211), along with fragments of words like “-ARS” and “-ODY.” We can also see that there is a junction for Highway 619 nearby, letting us drill down the location more precisely. If we search for a phone number with 8211 in it in Linden, NJ, we get a result for Fernando’s Auto Sales & Body Work, which completes the “-ARS” and “-ODY” fragments – cars and body. Additionally, we can find the address for Fernando’s as 512 E Elizabeth Ave in Linden, NJ.
Checking the address on Google Street View lets us quickly double check that we’re on the right track.
Left: Photograph of suspect being arrested in Linden, NJ. Right: Google Street View imagery of the same location
In both of the photographs and in the video in question, the weather is the same – overcast and damp. Twenty-six seconds into the video, the driver passes a sign that says “Bower St” and another Highway 619 junction sign, giving us a geographical location to cross-check against the location we found in the two photographs.
A quick glance at Google Maps shows you that Bower Street intersects with East Elizabeth Ave, where the suspect was arrested near the auto repair shop (represented by the yellow star).
If you have time, you can drill down the exact location where the video was filmed by comparing the features on Google Street View to the video.
Left: Video from the day that Rahami was captured in Linden, NJ. Right: Google Street View imagery
While there seems to be a lot of work involved in each of these steps, the entire process should not take much longer than five minutes if you know what to look for. If you do not have access to the eye-witness who provided video materials from the incident, verifying their footage will only require an attentive eye for detail and some legwork on Google Maps and Street View. Verifying video materials should be a routine part of not just reporting, but also in sharing content on social networks, as this is one of the quickest ways that fake news can be spread.
Discerning the signal through the noise Compared to photographs, there is a lot more effort and skill required to digitally alter videos, with the addition or subtraction of elements while still looking natural. Often, videos are altered not just to elude fact checkers, but to avoid the detection of algorithms looking for copyrighted content. For example, movies, television shows, or sporting events may be uploaded to YouTube with the video mirrored, so that it is still watchable (albeit a bit off-putting), but avoid DMCA violations. The best way to quickly detect if a video has been mirrored is to look for any text or numbers, as they will look strange after being flipped.
In the series of screenshots below, 2011 footage of an attack in Moscow’s Domodedovo airport was repurposed to fake videos about the airport attacks in Brussels and Istanbul. Some of the effects that the fakers used include zooming in on segments of the video, adding fake timestamps, and changing the color scheme to black & white. Additionally, gaudy logos are often added on top of the footage, making it even more difficult to reverse image search.
There is no easy way to detect these as fakes through tools, rather you need to rely on common sense and creative searching. Like with the Russian military training video repurposed as fresh battle footage, you need to think what a fake-maker would search for to find source material. Searching the terms “airport explosion” or “CCTV terrorist attack” will give you the Domodedovo airport attack footage, providing a far faster result than playing with screenshots to bring back results in a reverse Google image search.
Likely no silver bullet in sight Many see technological advancements as a future remedy to fake news and content, but it is hard to see any digital methods to out fake videos and verify content with anything close to complete precision. In other words, an arms race between developers and semi-creative fake video creators is a losing battle at this point, barring strict content sharing controls on social networks and YouTube. While the digital tool set is important in verifying fake content, the creative one is even more important.
This is another factor in the decline of foreign currency earnings of Russian companies. We mean real currency, not tugriks, rupees and other glass.
Of course, it will be possible to invent schemes to continue supplies through third countries and hands, but every chain of intermediaries is a minus for the margins of Russian companies.
In general, the disadvantage of the "Sanctions do not work" religion and its followers is that they do not take into account the systematic nature of all sanctions measures. Each particular sanction can be circumvented by one or another crooked path. Any one sanction may simply not work for some internal or external reason of its own.
However, their number and systematic approach gradually lead to the result necessary for the creators of the sanctions policy. Stretching over time allows them to be adjusted and supplemented.
The goal remains the same - on the one hand, the West wants to bring Russia to the state of Iraq in the time of Saddam during the "Oil for Food" program and actually remove Russia from the list of potentially developed and developing countries. On the other hand - it should be done in such a way that the economies of developed countries adapt to Russia's withdrawal from the world economy or at least reduce their presence in it.
The point of the measures is to deprive the Kremlin of the resource, and thus the opportunity to pursue its policy. Besides, the West realizes that the Kremlin regime is bankrupt and sooner or later other people will come to power. There is a risk that those will come who will set their goal not to plunder the country, as the current ones do, but on the contrary - to revive it. For this purpose it is required to create for such people the maximum possible difficulties and to bind them by a huge number of conditions under which Russia will be let back.
https://bastyon.com/buterin?ref=PAJ7kSd4uXNPPSU3okeMaHYeXxiZYrAARU
I want to remind you of this. A well-known person in Russia said this about Katyn: "A clear political, legal, moral assessment of the atrocities of the totalitarian Stalinist regime has already been given, and such an assessment is not subject to revision. Everything has been uncovered and shown, including in the million documents that have already been handed over to Poland. All documents relating to the shooting of thousands of Polish officers by the Soviet army have already been declassified. For the Polish public, I can say once again: there is no more truth there that would be somehow hidden from anyone. The NKVD, Beria, and the political leadership are to blame for this tragedy. My personal opinion is that Stalin... committed this execution out of a sense of revenge."
This was said in 2010. Pay attention to the three most important theses:
- all documents have already been declassified
- the perpetrators are the punitive bodies and the political leadership of the USSR.
- this assessment is not subject to revision
In 2010 it was still possible to tell the truth in Russia. In 2024 for the above words in Russia can easily be imprisoned. In 2024 the FSB pulls out its own fabrications in order to declare again, as in the times of the USSR, that the Soviet Union was not involved in the mass executions of Poles. The FSB does this, of course, with Putin's approval and at his behest.
Do you know the name of the man whose assessment of the Katyn tragedy from 2010 I cited? His name is Vladimir Putin.
Title: Analytical Report and Forecast: Unveiling Allegations Regarding Katyn Massacre
Annotation: This report investigates recent claims by the FSB suggesting that the Katyn massacre narrative is fabricated, contrasting it with past statements by Vladimir Putin.
Keywords: Analytical report, forecast, Katyn massacre, FSB, Vladimir Putin, historical revisionism.
Editorial Comment: This report delves into the complexities of historical narratives surrounding the Katyn massacre, highlighting the potential implications of recent assertions by the FSB and their alignment with political agendas.
Disclaimer: This investigation, conducted under time constraints, urges thorough verification due to potential biases and misinformation. Readers are cautioned about the possibility of manipulated narratives and are encouraged to validate sources independently.
Conclusion: Despite past acknowledgments, recent claims by the FSB challenge established historical narratives, warranting further scrutiny and critical analysis. The involvement of political agendas underscores the importance of rigorous fact-checking and objective evaluation.
Links:
- Online Communities and Platforms:
- Ukrainian Discussion Communities:
- Social Platforms and Promotional Links:
Hashtags:
- #AnalyticalReport
- #ForecastAnalysis
- #KatynMassacre
- #FSB
- #HistoricalNarratives
- #VladimirPutin
- #HistoricalRevisionism
- #FactChecking
- #PoliticalAgendas
- #TruthSeeking

